How to Crack Zip Passwords: A Guide to Password Cracking
Disclaimer:
This article is meant for educational purposes only. Attempting to
crack zip passwords without proper authorization is illegal and unethical. It
is important to always respect the law and use this knowledge responsibly.
In our increasingly digital world, the importance of robust
passwords cannot be overstated. Weak passwords pose a significant security
risk, and there are instances where individuals find themselves locked out of
their own files or accounts. But what do you do when you need to access a
password-protected zip file for legitimate reasons, such as recovering
forgotten passwords or regaining lost access? In this comprehensive guide, we
will explore how to crack zip passwords using a powerful tool called John the
Ripper. Along the way, we will emphasize the critical importance of strong
passwords and illuminate the disadvantages of using weak ones.
Cracking Zip Passwords Using John the Ripper
Now, let's explore the process of cracking zip passwords using John
the Ripper. Please note that this information is for educational purposes only,
and attempting to crack passwords without proper authorization is illegal.
Step 1: Locate the Zip File
Before you can begin, you need to have the zip file you want to
access. Make sure it's in the directory you're working in.
Step 2: Obtain the Zip File Hash
To crack the zip password, you first need to obtain the hash of the
zip file. Use the following command:
zip2john zipfile > output.txt
Replace "zipfile" with the name of your zip file and
"output.txt" with any name of your choice in .txt format. After
executing this command, you will have a .txt file containing the hash of the
zip file.
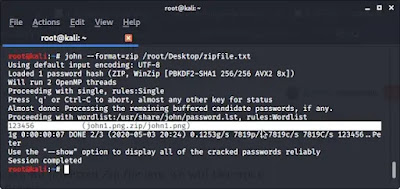
Step 3: Password Cracking
To crack the zip password and potentially recover the password,
you'll use John the Ripper. The command you need depends on the hash format.
For a typical zip file, you can use the following command:
john --format=zip hashfilepath
Replace "hashfilepath" with the path to the .txt file
containing the hash you obtained in Step 2.
It's important to note that cracking a password-protected file can
take time, especially if the password is strong. The duration depends on the
complexity of the password and the computing power available to John the
Ripper.
The Importance of Strong Passwords
It's crucial to
understand the significance of using strong passwords for your digital assets.
Strong passwords are your first line of defense against unauthorized access,
and they play a critical role in safeguarding your data and personal
information. Here are some key reasons why strong passwords are essential:
- Security: Strong passwords make it much more
challenging for malicious actors to crack zip passwords and gain unauthorized
access to your files and accounts. They act as a barrier against common
password-cracking attempts.
- Data Protection: Your digital
files may contain sensitive or personal information you want to keep
confidential. Strong passwords ensure that only authorized individuals can
access this data.
- Privacy: Protecting your online presence
and accounts is crucial for safeguarding your privacy. Strong passwords help
you maintain control over your online identity.
- Preventing Identity Theft: Weak
passwords can lead to identity theft, where an attacker impersonates you and
misuses your personal information for fraudulent purposes. Strong passwords are
an effective deterrent against such activities.
- Legal Compliance: In many
jurisdictions, organizations are legally obligated to use strong passwords and
security measures to protect sensitive information. Non-compliance can lead to
legal consequences.
The Disadvantages of Weak Passwords
Conversely, using weak passwords can lead to a myriad of problems
and vulnerabilities, including:
- Vulnerability to Password Cracking: Weak passwords are easy for hackers to crack, including zip password
cracking, putting your accounts and data at risk.
- Data Breaches: Weak
passwords are a leading cause of data breaches, where sensitive information is
exposed or stolen. This can lead to financial losses and reputation damage.
- Identity Theft: Weak passwords
make it easier for cybercriminals to steal your identity and engage in
fraudulent activities on your behalf.
- Account Takeover:
Cybercriminals can take over your accounts, change passwords, and lock you out,
causing significant inconvenience and potential financial losses.
- Loss of Digital Assets: If you forget a weak password or cannot recover it, you risk losing access to important digital assets, including documents, photos, and files.
Conclusion
While it's possible to crack zip passwords using tools like John
the Ripper, it's important to emphasize that attempting to crack passwords
without proper authorization is both unethical and illegal. Strong passwords
are crucial for maintaining the security and privacy of your digital assets and
should be used to protect your data.
Ultimately, the best practice is to always use strong, unique
passwords for your files, accounts, and online services. Consider
using a reputable password manager to help you generate and store complex
passwords securely. It's essential to respect the law and use your knowledge of
password cracking responsibly, ensuring that you only access files and accounts
for which you have legitimate authorization.